-
Call Us: +91 9820073878
info@itanalysis.in
Call Us: +91 9820073878
info@itanalysis.in
Vulnerability management is a cyclical process of identifying IT assets and correlating them with a continually updated vulnerability database to identify threats, misconfigurations, and vulnerabilities. Another aspect of vulnerability management including validating the urgency and impact of each vulnerability based on various risk factors and responding to the critical threats swiftly.
VM Tools works with the groundbreaking cloud agents. Extending its network coverage to assets that cannot be scanned. The lightweight, all-purpose, self-updating agents reside on the assets they monitor - no scan windows, credentials, or firewall changes needed, vulnerabilities are found faster, and network impact is minimal.
When VM Tools is paired with continuous Monitoring (CM), it will proactively be alerted about potential threats so problems can be tackled before turning into breaches. CM gives you a hacker's eye view of your perimeter, acting as your cloud sentinel.
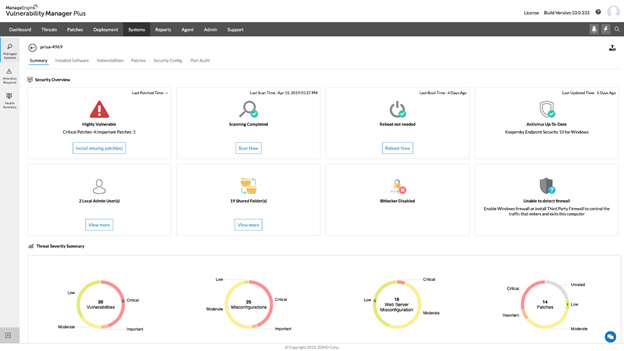
VM continuously scans and identifies vulnerabilities with accuracy, protecting your IT assets on premises, in cloud and mobile endpoints. Its executive dashboard displays an overview of your security posture and access to remediation details.