-
Call Us: +91 9820073878
info@itanalysis.in
Call Us: +91 9820073878
info@itanalysis.in
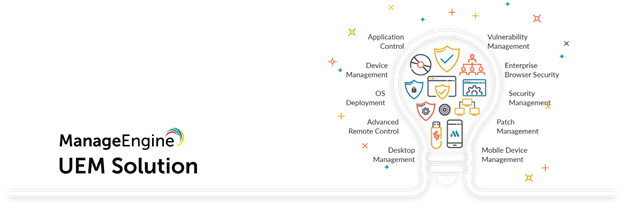
Manage your enterprise endpoints, including servers, desktops, laptops, smartphones, and tablets, from a central location.
Solutions to secure all endpoint devices accessing your organization's network from insider threats and vulnerabilities.
End-point securities tools makes all devices visible verifies their identity and determines whether they pose and securities threats.
Accurate identification and profiling of endpoints support network segmentation--a key part of the zero-trust security framework. Network segmentation benefits organizations by reducing overall risk, shrinking the scope of compliance, and limiting the lateral movement of malware to contain threats such as ransomware.
Despite the benefits of segmentation, many organizations have been hesitant to segment their networks widely,since the process can be complicated and error prone. Endpoint analytics tools can serve to lower the barrier to effective segmentation.
While every organization would benefit from implementing robust security for IoT devices, those with data-privacy, security, and Regulatory compliance mandates--such as healthcare and financial institutions--should seriously consider deploying endpoint analytics. Industries that use many IoT devices--such as manufacturing, transportation, smart cities, and utilities--would also benefit.